Security is Even the Responsibility of Your Software Provider
June 04, 2020 | 2 min read

Cyber threats continue to grow exponentially each year. This new normal has made the real ramifications of an attack seem common-place. However, it is vital for an organization to take security seriously and put measures in place that mitigate risk, while also protecting their reputation, their finances, and ultimately their ability to do business.
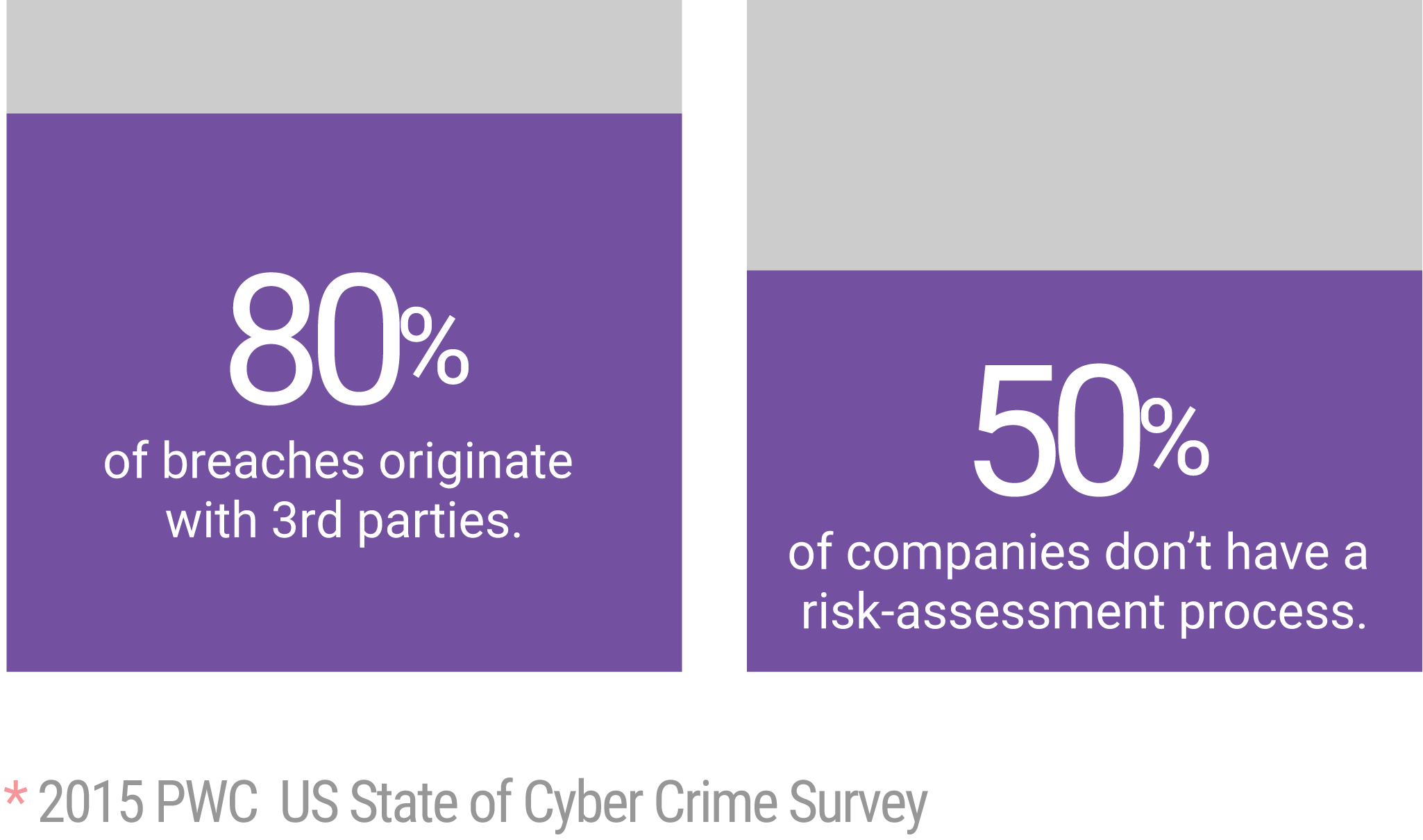
Many organizations turn to cloud computing solutions because of their ability to provide enterprise features, like security, that many organizations simply can’t afford. This rise in cloud computing interest has led to a flurry of new e-procurement software platforms. While some are equipped to handle an attack, many lack security features and leave organizations vulnerable.
Here are some easy steps to get organizations to begin evaluating potential security threats and evaluating solutions to mitigate future attacks.
Step 1: Create a Comprehensive Incident Response Plan.
Strong planning and communication can go a long way in keeping an organization secure. The first place to start is to bring together all relevant stakeholders, including leadership, IT, employees to identify threats, implement priority risk solutions, and a roadmap for continuous improvement. However, the harsh reality is that even with those measures it is likely that an organization will be attacked. Given that reality, it is important that while planning to protect an organization, to also consider how to address a security incident quickly and comprehensively. Simply ask questions like, who will handle communication with partners and customers, what recovery activities will be started and how will the status be communicated.
Secure transactions are essential if organizations are to fully realize the benefits of e-procurement.
Step 2: Add definition and community knowledge to basic security practices.
Organizations need to raise awareness among employees and protect their community - let the community know that customers require the most vigilant security practice and that their support ensures the organization’s ability to grow.
Whether it is helping employees understand that it is essential to change passwords every 90 days, or why more cumbersome security policies are now necessary, it is essential to communicate clearly and often.
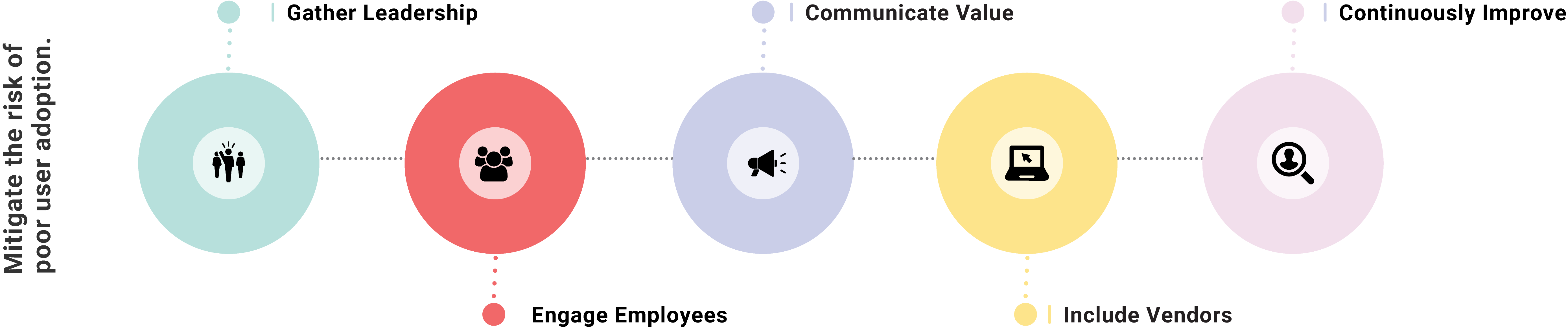
Step 3: Require security assurances are a part of vendor agreements.
Third-party vendors must be held to the same - if not higher - level of accountability than your actual employees. Organizations should consult with their legal teams to add security elements into vendor and partner agreements - such as an incident response plan and data security policy, in addition to requiring all third parties to test those plans in joint exercises.
ProcurePort not only implements comprehensive security measures, but they also have security compliance experts that can help to establish strong policies and communication. Start here to strengthen your organization’s supply-chain and place in the market.
75% of the buyers in the Procurement industry are not currently using e-Procurement software at work.
For more insight,
The Definitive Guide to
Procurement Software
breaks down selecting,
implementing and leveraging a
modern e-Procurement solution.

